Be it a simple theft or a meticulously planned dark web crime, the same approach must be undertaken when trying to solve the case. The place to start is with research. In the simplified guide presented below, you will learn how to investigate a crypto crime by applying blockchain analysis and using open source intelligence.
Step 1: Create a Timeline
Investigating a crypto crime starts with collecting and arranging source information. This primary research should be focused on answering as many W-questions as possible: who, what, where, when and why. As a rule, the subject, location and motivation (one of which is usually missing) should be explored, developed and verified in the hopes of creating a sound hypothesis.
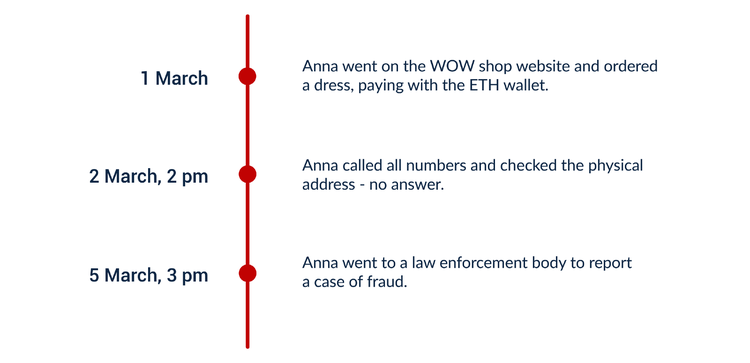
In terms of structure, law enforcement’s preferred way of arranging input information is by creating a timeline with a sequence of events. Each point in the scheme represents a separate action and requires supporting evidence, which can be added later.
In the simplified case of Anna above, you can see that most likely she was the victim of a fraudulent online shop. You know the amount she has lost and, what is more important, the wallet address of the beneficiary. This is where the next step occurs — blockchain analysis.
Step 2: Analyze Wallets & Transactions
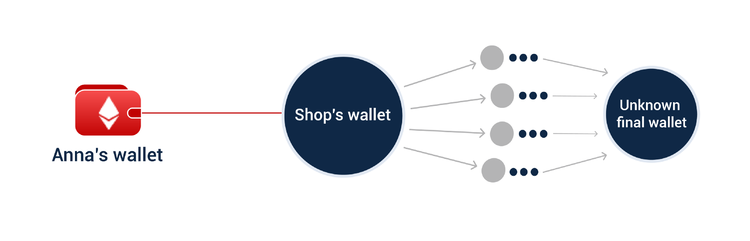
Transaction analysis is a central part of any crypto investigation, as you can not only follow the money, but also establish the origin and which tools were used when perpetrating this particular financial crime. In-depth examination of a blockchain address is indispensable when it comes to spotting accounts that belong to the same owner (also known as clustering). Discovery requires taking a closer look at coordinated “coincidences” such as those that occur with time, volume, destination, or regularity of transactions.
In the case of open-ledger blockchains, investigating addresses is child’s play. To analyze a Bitcoin or Ethereum transaction, you can use any wallet explorer or open-access blockchain analytics tool like ORS CryptoHound. With the help of the former, you can learn a wallet’s balance, value and detailed history of transactions. By using the latter, you can dig deeper into related addresses and reveal patterns or suspicious interactions.
Our sample investigation for Anna continues! The second step of our blockchain analysis showed that the vendor in question had been using a cluster of addresses to hide the movement of funds. We followed the money until we reached the final beneficiary. Identifying its owner brings us to the next step of the investigation — blockchain intelligence from open sources.
Step 3: Add Data from Open Sources
Interpreting previously collected evidence is the final and most demanding stage of the research. This requires both expertise and intuition, as well as solid research from open sources. In order to assemble the last piece of the crypto investigation puzzle, you can use:
- OSINT (Open Source Intelligence) tools for discovering associated locations, e-mails within the domain and more: Recon-NG, Belati, Trape, FOCA, Cree.py, Harvester or Maltego;
- Custom searches on Google, Yahoo, and other search engines;
- News articles from leading crypto media (Cointelegraph, Coindesk etc.);
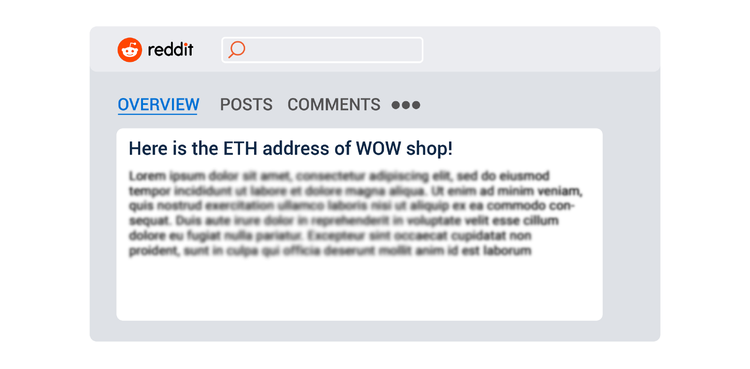
- Social networks (think of Twitter or Reddit disclosures of blockchain addresses!);
- Blockchain explorers with labeled addresses (e.g. the publicly known wallets of crypto exchanges, which are commonly listed on websites such as Etherscan).
Getting back to Anna’s case, we had some success! A whole subreddit emerged with regards to the fraudulent online shop, where people identified the ultimate beneficiary. It appeared to be a teenage girl who could not afford to buy branded clothes, so she decided to take revenge on those who could. Case closed!
Further Steps
Once you have identified the person behind the crime and added evidence from blockchain analysis and open investigations, you can summarize the findings in a formal investigation report. The completed dossier can then be used to either directly contact the party responsible in an effort to reclaim funds, or presented to law enforcement authorities, in the hope of proceeding with any litigation procedures.
Closing Statement
This brief guide on investigating crypto crimes was prepared for general reference and does not claim to be any form of professional advice. We hope you don’t have to resort to it — unless for personal interest!