Developers of the cryptocurrency Montero have eliminated a bug that could allow intruders to "burn" funds in organizations' wallets while sacrificing only a modest amount in the form of transaction commissions. This is reported in the official announcement of the project.
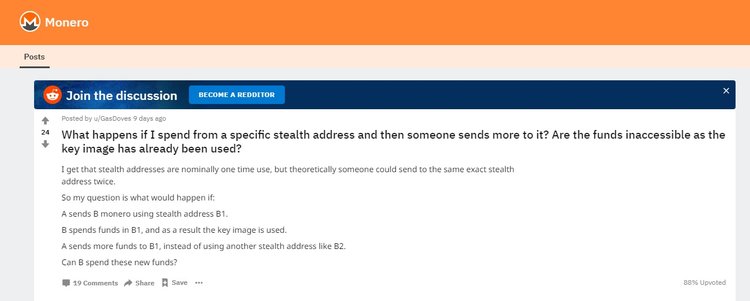
Identifying the bug has been made possible thanks to a scenario of a hypothetical attack described by one of the users on the Monero subreddit. A participant asked what would happen if you sent a lot of transactions to the so-called stealth address. In an attempt to answer the question, the developers discovered a vulnerability in the monero code. The stealth address is one of the methods for ensuring the confidentiality of transactions in monero. With its help, the recipient can receive an unlimited number of public payments for one published address which will not be tracked.
A bug was addressed via a software patch and first distributed privately between exchanges and the merchant and then publicly disclosed through an autopsy on the project website. It allowed the intruder to deliberately "burn" the XMR by sending several payments to the same hidden address. This the recipient could spend the same coin a second time. As a result, funds sent through subsequent transactions would be transferred to the category of insolvent because these transactions would lead to duplication of keys that would be rejected as alleged double attacks.
Although there is no direct benefit in such actions, the project team assumes that the attackers could have other interests. For example, after an attack using a stealth address, they could conduct one exchange of XMRs for bitcoins and withdraw them leaving the exchange with burned coins.
Currently ,the mentioned monero vulnerabilities have been fixed. Disclosure of the error had no significant effect on the price of the altcoin. It’s now trading at the level of $115, the price of XMR has decreased by 2,5% per day.
Monero is often praised for its reliability. But despite this, a number of vulnerabilities have already been discovered. One of them allowed hackers to steal coins directly from wallets on the exchanges. Hackers forged data about transactions and used it to deceive the support and charge XMR through social engineering.
Monero is also very fond of hidden miners. As of the middle of this year, 5% of altcoin emissions were mined with the help of malicious software. The study showed that scammers use the computing power of victims for monero mining in 85% of cases and only 8% of attacks are aimed at mining bitcoin. In most cases, hackers mine cryptocurrency with the consent of users who have given access to their capacities (albeit unconsciously), or through browser scripts, for example, Coinhive.
According to a recent study by Cyber Threat Alliance, a cyber-security firm, the cases of hidden cryptocurrency mining increased by 459% compared to the previous year. "If miners can gain access to use the processing power of your networks, then you can be assured that more sophisticated actors may already have access. Illicit cryptocurrency mining is the figurative canary in the coal mine, warning you of much larger problems ahead," the document says.
Subscribe to our Telegram channel to stay up to date on the latest crypto and blockchain news.